UPDATE – 25/05/23:
A new risk has been discovered with the new .ZIP Domain – Software, website’s etc has had the ability to convert plain, simple text that denotes anything that could be a website URL. So if you were to go onto Facebook, write a post with “example.com”, then post without any linking, Facebook will commonly change that example.com into a clickable/tappable link to example.com.
This discovery means that past posts, emails, anything that converts plain text into URL links based on profiling the words as a potential link, runs the risk of turning any mentions of .ZIP files into links, thus taking you to the domain.
If used properly, someone may end up opening a past link that downloads a malicious file or goes to a phishing webpage to grab info from you.
We also did not mention another Domain from Google – .MOV. .MOV is a file type related to the Quicktime Video Format. Just like .ZIP, .MOV can be exploited in the same way.
.ZIP is the more common and the most concerning, because of the nature of this file type and what it does.
Today’s topic is Google’s new Top Level Domains, specifically .ZIP.
Now, for some of you, ZIP may sound familiar. ZIP is used as a file type for compressed files and folders. We wont get into too much details, other than it is a format to compress data to make it “smaller”.
Google has brought out the Domain of ZIP as a symbol for short, powerful, trackable links. This however has caused some very valid concerns in the Cyber Security Community.
Let’s jump right into why.
First, lets quickly learn about Domains.
Domain name is the address of your website that internet users type in the browser URL bar to visit your website.
In simple terms, if your website was a house, then your domain name will be its address.
Our address is “cpkncomputers.com.au”.
In Australia, our Top Level Domain (TLD) and Country Code (ccTLD) is .au.
TLD is used to help identify, organize, and classify websites based on their content, purpose, or location. So .gov.au would indicate that the address relates to the Government, while a .au means the origin of the resources should be from Australia.
let’s have a look at the common malicious use for the .ZIP Domain.
In the example above, is something someone could simply link to you that leads to a malicious website or file download, putting you at risk.
If someone isn’t concentrating, you may mistake a ZIP file type over a domain.
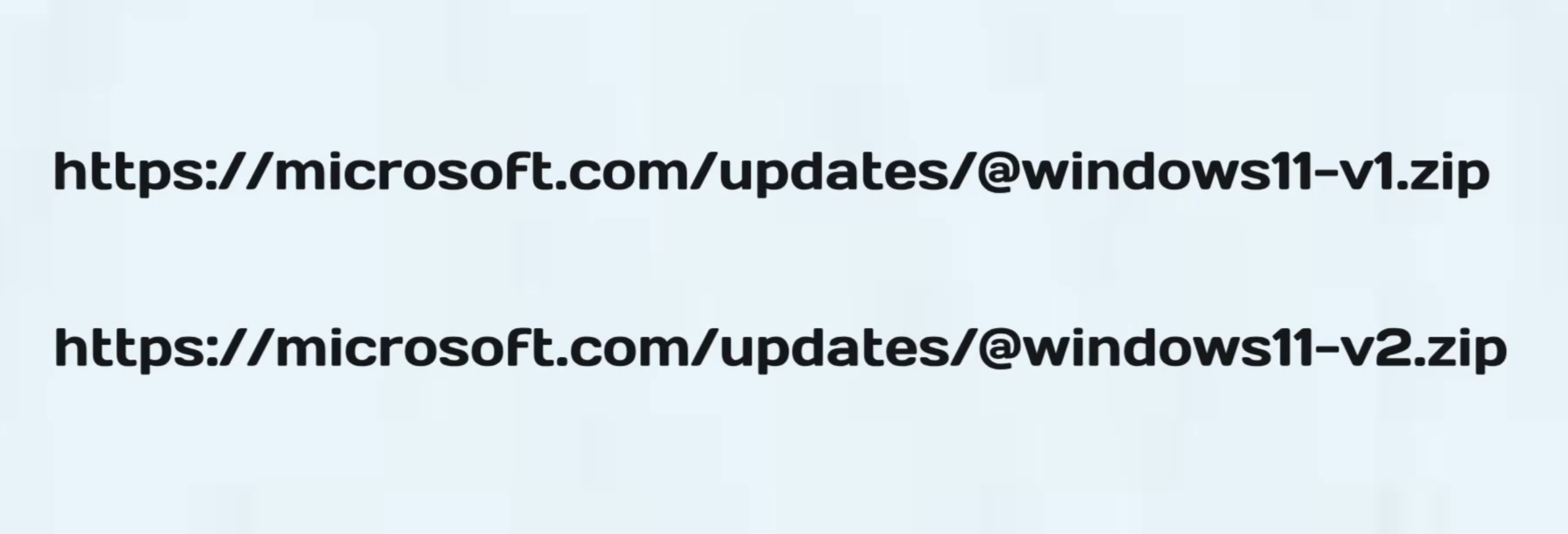
Now lets look at these 2 URLs for a moment:
They look very standard, nothing has been altered to trick you like changing letter L for I, for example.
Can you spot which of them is real and which is fake?
Now, the common answer some of you may say is the @ symbol being the odd thing out, and you would be correct, BUT for the wrong reasons.
Let us show you another 2 URLs – we want you to check to see if you can tell which is fake or which is real:
This time, it was a trick question, because both are fake.
So you then might be asking how? They look fine, no red flags pop out? Well, this is where things get more fancy at tricking you.
Thanks to Security Researcher Bobby Rauch (@bobbyrsec), Bobby pointed out that there is an old feature that most web browsers support that allows you to use a syntax in URLs to help with this trick.
It looks something like this:
username:[email protected]
You have the username, then a colon, the password and then the @ symbol, which will help treat everything before as user info, then at the end is the host.
In this example, we used yourdomain.com.au as the host, but then if we change .com.au to .zip, this is where it can turn problematic.
Lets build the malicious URL.
first, you will notice that username and password has a colon in between. URLs have this in the beginning with HTTP and HTTPS.
So the scammer would then make the username HTTPS.
Next, the password would be the host, so you would make it //cpkncomputers.com.au/.
then finally, you put the @ symbol and then your malicious ZIP domain, like a filename.
Now we have a legitimate looking URL:
https://cpkncomputers.com.au/update.zip
2 things going against this method, is the fact that Browsers should treat the info after the @ as the host, and will therefore goto that domain.
If you were to add slashes after the initial domain and have it point to a sub folder, like this:
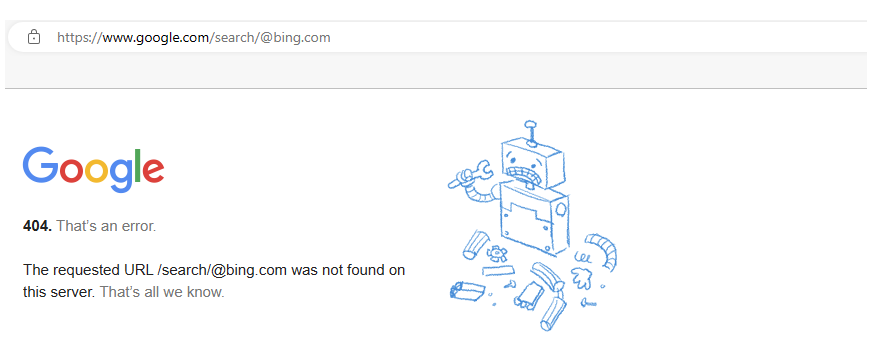
https://google.com/search/@bing.com
Then those slashes will be treated like it is the host domain that ends up making you go to something like this:
Obviously the goal of a hacker/scammer would be to try and execute a download, so this would not help. but this is where another issue comes in.
There is a system called Unicode, which is an information technology standard for the consistent encoding, representation, and handling of text.
Sadly enough, there are Unicode slashes that can be used where the browser doesn’t treat it as standard slashes, which means now the hosting domain after the @ symbol can be executed and the slashes before are ignored.
U+2044 (⁄) and U+2215 (∕)
so now you can have these on your URL and have the .ZIP domain execute to download a malicious file or a webpage to phish information from you, like usernames and passwords.
To add insult to injury, depending on how you receive the link, actors can reduce the size of the @ symbol and try to change the font colour to white in an attempt to hide 1 of the possible checks you can do against this trick.
So, what to do moving forward…
Hopefully, you are already doing checks to links to ensure they are looking legitimate, which can normally be done by hovering over the link to get the tool tip that tells you the URL.
First off, if the link is going to a .ZIP domain, you should highly consider whether or not you want to navigate to this.
Next, check if the Link and/or URL has an @ symbol in it, especially closer to the .zip part.
Since there is a chance of shrinking and whiting out the symbol, another way to verify is to copy the link and then paste it into Notepad for Windows or TextEdit for Mac, however, for TextEdit, you must make sure it will show the text in plain format by going to File and ensuring that Ignore Rich Content is active.
For Mobiles and Tablets, you can paste the link into the Text Messaging App and that should ignore the font colour and size.
We hope this was informative and please be careful when it comes to opening links. If you have any questions or concerns about your Personal or Business Security, contact us ASAP so we can help rectify any shortcomings.