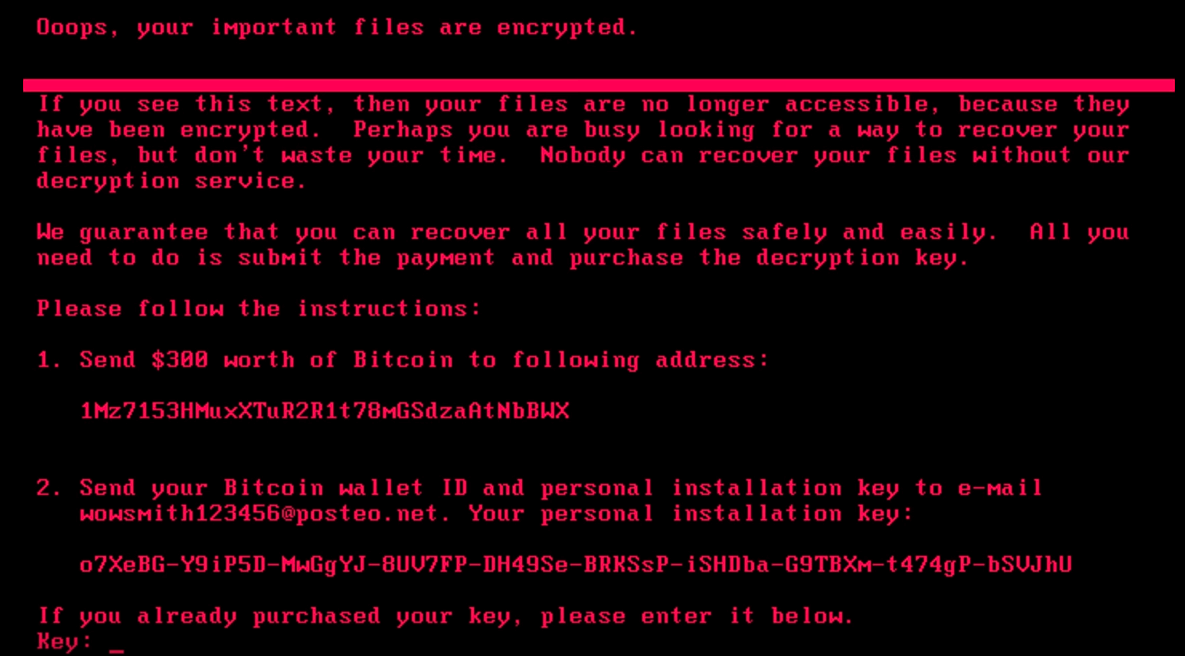
A new ransomware variant is spreading quickly across the world.
The ransomware has been dubbed “Petya”. It likely spreads by using two separate exploits. You don’t need to click on anything or take any action.
This can spread into your system through the network. That is why it is having such a wide impact and why it is important that you update your system to protect yourself.
For the technically minded: This ransomware is exploiting a vulnerability in Microsoft Office when handling RTF documents. It also exploits a vulnerability in SMBv1 which is the Microsoft file-sharing protocol. This second vulnerability is described in Microsoft security bulletin MS17-010 – related to the WannaCry Ransomware.
The ransomware has affected a large number of companies, organizations and government entities on an international scale.
You are confronted with a screen that looks like the image at the start of this post.
What To Do
If you have not done so already, you should immediately install the MS17-010 patch from Microsoft.
If you currently run an unpatched Windows system, you may not have time to patch it before you are infected. Consider shutting down your machine and leaving it off the network until there is more details on fully preventing it.
Engineer Amit Serper has figured out a “vaccine” to help stop this Ransomware, but it is unclear how affective it really is until more results are made.
https://twitter.com/0xAmit/status/879778335286452224 (Tweet Deleted)
Amit discovered that if a file exists, the encryption routine will not run.
To vaccinate a machine against this ransomware, simply create a file called perfc in the C:\Windows folder and mark it read only.
A post BleepingComputer has instructions on how to create the file manually if you would prefer to do that, otherwise contact us for support.
Once this file is created, the encryption routine for this specific ransomware variant will not run and encrypt your files.
Update your anti-virus definitions and run a scan on your system. If you are a Norton Security owner, you will already be safe thanks to Norton SONAR and updating their Virus Definitions.
Who This Has Affected So Far
- A Ukrainian state power company and Kiev’s main airport were among the first to report issues.
- The Chernobyl nuclear power plant has had to monitor radiation levels manually after they were forced to shut down the Windows systems that their sensors had been using.
- Antonov aircraft has reported being affected.
- Copenhagen-based shipping company Maersk is experiencing outages in multiple IT systems and across multiple business units.
- Food giant Modelez, which makes Oreo and Toblerone, has also been hit.
- Netherlands-based shipping company TNT was also hit.
- French construction company St. Gobain has been affected.
- Pharmaceutical company Merck says they have systems affected.
- Law firm DLA Piper was hit.
- Heritage Valley Health System, a US hospital operator, has also been hit.
- Kiev’s metro system has stopped accepting payment cards because they were affected.
- Australian businesses including courier companies, legal firms and even Cadbury.
The list is long and growing; the above is just a snapshot.
We shall keep you posted as more develops.