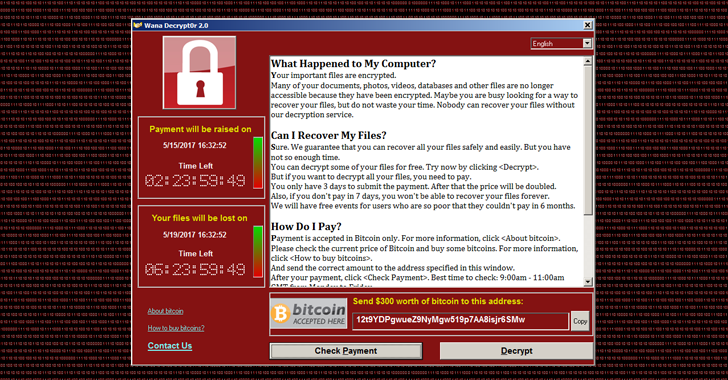
On Saturday, we reported and alerted everyone about a huge attack on many countries using a Ransomware called “WannaCry” or “WannaCrypt0r”. A few hours ago, reports have come in that a second wave has hit with a variant of the last attack. The second wave and many other potential ones are a worry as many head back to work today.
The variant has been reported to be stopped yet again, thanks to registering the Domain Name that the attackers are using to execute the attacks.
It has now affected more than 150 countries, including the UK, US, China, Russia, Spain, Italy and Taiwan, with over 200,000 cases of people/organizations being affected.
The Hon Mr Dan Tehan MP – the appointed Minister Assisting the Prime Minister for Cyber Security, had announced on ABC News Radio that 3 Australian Businesses were affected, but did not disclose the names and when.
UPDATE: A Hacktivist Group named “SpamTech” have made claims to the WannaCry Ransomware:
https://twitter.com/0xSpamTech/status/863058605473509378 (Tweet Delete)
When asked for proof, they have not responded as of yet. The interesting part about the language is the fact it says “we have taken over NHS…” rather anything related to making money or causing a huge issue.
We shall keep you posted.
What to do? Am I Protected? More Details?
Microsoft made a patch last month to counter this issue, however many people who do not stay on top of Updates, including Businesses, are likely at high risk.
Some Points to follow:
- If you use Windows, install the patch that Microsoft has released to block the specific exploit that the WannaCry ransomware is using. You can find instructions on the Microsoft Knowledge Base. You can also directly download the patches for your OS from the Microsoft Update Catalog.
- Please Note: You might be using a Platform – such as Apple, that isn’t being affected by this Ransomware. However, Virus/Malware Deployment can vary and depending on the files and how you share them, means you can infect Windows Computers by attaching yourself to Networks and/or sharing infected files. Please be careful what you download and be sure Windows Devices around you are up-to-date.
- If you are using an unsupported version of Windows like Windows XP, Windows 2008 or Server 2003, you can now get the patches for your unsupported OS from the Update Catalog. We do recommend that you update to a supported version of Windows as soon as possible.
- Update your Antivirus software definitions. Most AV vendors have now added detection capability to block WannaCry.
If you don’t have anti-virus software enabled on your Windows machine, we recommend you enable Windows Defender which is free. We do recommend Norton Security Premium by Symantec. - Backup regularly and make sure you have offline backups. That way, if you are infected with ransomware, it can’t encrypt your backups.
- Want more details? Microsoft has released “Customer Guidance for the WannaCry Attacks” and Troy Hunt – an Australian Web Security Expert, known for creating the Data Breach Search Service “Have I Been Pwned?”, has done an amazing, detailed writeup on the WannaCry ransomware.