Mark Maunder, CEO of WordPress security plugin Wordfence, has reported on a new Gmail scam that is even fooling tech-savvy, security-conscious users.
A new highly effective phishing technique targeting Gmail and other services has been gaining popularity during the past year among attackers.
This attack is currently being used to target Gmail customers and is also targeting other services.
The way the attack works is that an attacker will send an email to your Gmail account. That email may come from someone you know who has had their account hacked using this technique. It may also include something that looks like an image of an attachment you recognize from the sender.
Mark Explains.
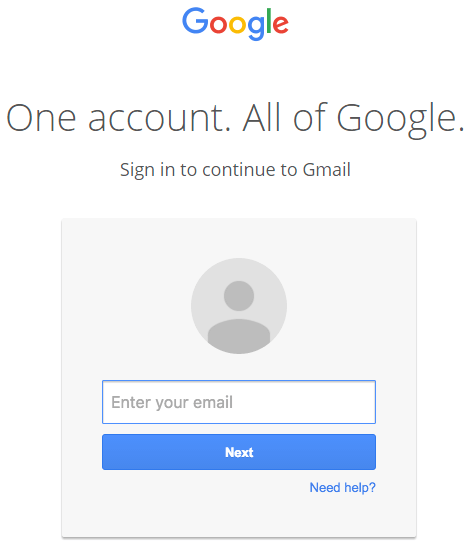
When you click on the image, you expect Gmail to give you a preview of the attachment. Instead, a new tab opens up and you are prompted by Gmail to sign in again. You view the location bar and you see accounts.google.com, and think “yep, cool” without realizing what the rest of it says… Like this:
The nail on the coffin is the fact you then see the legit looking Google Account Login Screen:
As simple as that, you are compromised.
A commenter on Hacker News describes what they experienced once they signed in to the fake page:
The attackers log in to your account immediately once they get the credentials, and they use one of your actual attachments, along with one of your actual subject lines, and send it to people in your contact list.
For example, they went into one student’s account, pulled an attachment with an athletic team practice schedule, generated the screenshot, and then paired that with a subject line that was tangentially related, and emailed it to the other members of the athletic team.
The attackers signing into your account happens very quickly. It may be automated or they may have a team standing by to process accounts as they are compromised.
Once they have access to your account, the attacker also has full access to all your emails including sent and received at this point and may download the whole lot.
Now that they control your email address, they could also compromise a wide variety of other services that you use by using the password reset mechanism.
This Phishing attack is being used to steal usernames and passwords on Gmail. It is being used right now with high success and this technique can be used to steal credentials from many other platforms with many variations in the basic technique.
How to Protect Yourself
First and foremost, you need to change your habits with URL’s and what to look for. Sure, its annoying as hell, but you really need to skim URL’s before accepting it as safe. Anything you are not sure of, then leave it be.
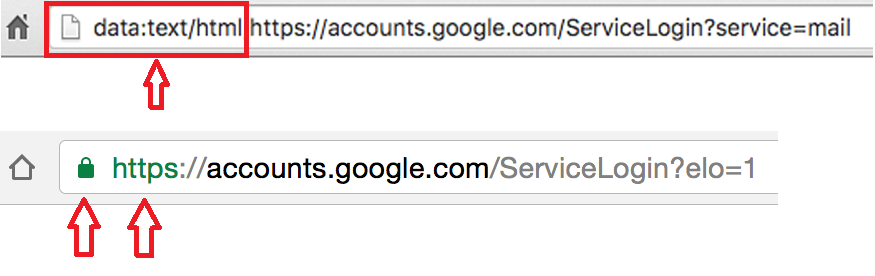
In this scam, you can immediately notice a difference:
Make sure there is nothing before the hostname ‘accounts.google.com’ other than ‘https://’ and the lock symbol. You should also take note that depending on the browser, you may see a green colour on the https and lock symbol, helping you visually know it is legitimate. If you can’t verify the protocol and verify the hostname, stop and consider what you just clicked on to get to that sign-in page.
Enable two factor authentication if it is available on every service that you use. Gmail calls this “2- step verification” and you can find out how to enable it on this page.
Enabling two factor authentication makes it much more difficult for an attacker to sign into a service that you use, even if they manage to steal your password using this technique.
Please share this post to your friends and family who have Gmail. It is important to be well informed to minimize the damage this attack does.
Remember, you might think you could not be fooled, but it has been highly successful to even the most savvy users out in the world!
Ransomware
According to Fortinet researcher Kai Lu, a new ransomware family is targeting Android devices, locking access to the screen, and constantly pestering the user to enter their payment card details.
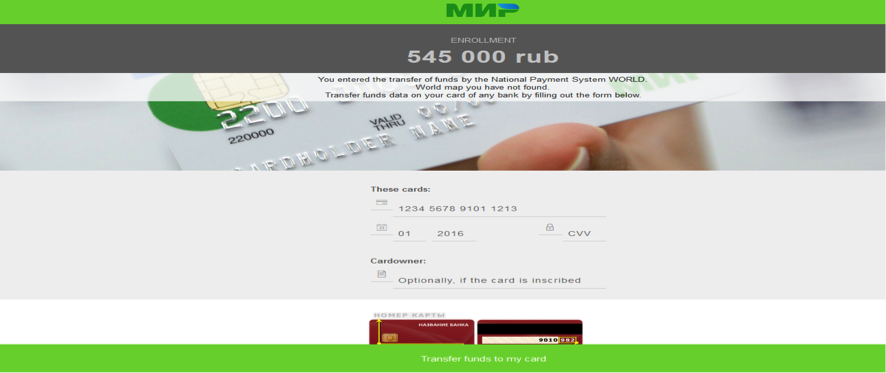
The ransomware appears to be targeting only Russian-speaking users so far, as its ransom note is only available in Russian. A translated version of the ransom note is available below:
While it has hit Russia, it is a concept that could spread around the world.
However, there are some points about this threat that is unusual to normal standards of Ransomware.
One, the ransom demand asks for 545,000 Russian Rub ($9,100USD).
This ransom demand is goes overboard rather good, subtle amounts. While some ransoms do ask or high amounts of money, this demand is higher than the price of new Android phones, and so most users who can’t remove the screen locker will instead choose to buy a new phone rather than paying the crooks.
Two, to pay the ransom, victims have to enter their credit card number directly in the ransom screen, a technique very different from how other ransomware operators like to work, which is via Bitcoin, Tor, or gift cards. With Credit Cards, Banks have a better chance to trace where the money goes and work with the crooks bank/s to freeze the funds and authorities can attempt capture.
It is using the Cloud!…
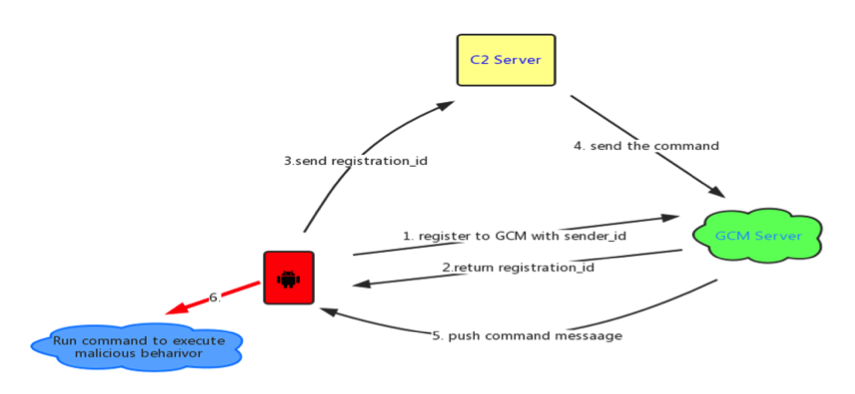
The other thing that sets this ransomware apart is the usage of the Google Cloud Messaging (GCM) platform, now renamed in Firebase Cloud Messaging (FCM).
The FCM is a service offered by Google to Android app developers. It allows app creators access to a service that takes pressure off their servers. A developer can send data from their server to the FCM, which then relays it to an app’s registered users. Vice versa, users can send data back to the developer’s server via the FCM.
Detected as Android/Locker.FK!tr, this ransomware uses the FCM in a similar manner, to take the load off its C2 server.
Infected phones contact the FCM platform, where they register and receive an ID, which they pass on directly to the ransomware C2 server. When the crook wants to issue commands to his victims, he simply relays instructions via the FCM platform, who uses PUSH notifications to tell infected phone(s) what actions to take.
According to Lu, crooks can send 20 types of commands to infected hosts, including – lock or unlock the device’s screen, add new contacts to the phone, steal all contacts, send SMS messages, and update the malware’s code.
As mentioned before, this ransomware is currently targeting only Russian users. Just like most Android malware today, this threat is hidden inside an app that requests users to give it administrator rights.
A somewhat lucky situation is, the app is likely installed from third-party app stores. Because the ransomware gets admin rights, users have to reboot their devices in safe mode and remove the app from there.
So a good rule of thumb is to only download Apps from Google Play and watch what you download anywhere.
Get a Security App on your phone like Norton Mobile Security by Symantec.
With Android being an Open Source Platform, malware and other attacks will keep popping up rapidly, especially with its popularity.